Decoding the Magic of RFID Cards
Introduction
In the fast-paced world of technology, RFID cards stand as beacons of convenience and security. These contactless wonders house an RFID chip that stores crucial data, transmitting it effortlessly through radio waves to be decoded by an RFID reader. Unlike their traditional counterparts, RFID cards don’t require swiping – just a moment’s proximity, and the transaction is complete in seconds!
An RFID card, which stands for Radio Frequency Identification card, is a type of card that uses RFID technology to store and transmit data¹.
Physical Properties:
- The primary RFID Card dimensions are known as “standard credit card” size, codified by the International Organization for Standards in the specification document ISO/IEC 7810 (Identification Cards–Physical Characteristics).
- The majority of RFID Card is still using plastic polymers as the base material. The most commonly used plastic polymer is PVC (Polyvinyl Chloride) due to its durability, flexibility and versatility for card making.
Technical Properties:
- Every RFID card embeds with an antenna that connected with an RFID IC, hence it can receive, store and transmit data via radio waves.
- RFID card usually is using passive RFID technology without an internal power source. The RFID card powered to work by the electromagnetic energy received that transmitted from RFID reader.
- There are four categories of RFID cards based on the difference between frequencies: Low Frequency at 125KHz RFID card, High Frequency at 13.56MHz RFID card, Ultra-High Frequency at 860-960MHz RFID card, and Combination of two or even three different frequencies into a single RFID Card.
In the context of credit cards, RFID technology enables contactless payments, one of the safest ways to pay. This contactless payment method is also referred to as Tap to Pay.
Types of RFID Cards
1. Active RFID Cards
With a battery-powered tag, active RFID cards continuously emit signals, ideal for tracking high-value assets in dynamic environments like toll stations. Their extended read range and constant signal emission, independent of an RFID reader, set them apart.
2. Passive RFID Cards
These cards lack internal power, relying on energy from an RFID reader. Widely used in access control and supply chain management, passive cards are cost-effective and activate only in the presence of a reader.
3. Semi-Passive RFID Cards
Featuring an integrated circuit and a battery, these cards offer a middle ground. While they lack an onboard transmitter like active cards, the added battery allows integration of real-time trackers, sensors, and notifications.
RFID Card Classification by Frequency
1. Low-Frequency (LF) RFID Cards
Operating at 30 kHz to 300 kHz, LF RFID cards find utility in environments with metals and liquids, despite their shorter read range.
2. High-Frequency RFID Cards
Within the 3 MHz to 30 MHz range, these cards boast better memory and an extended read range, making them suitable for applications like library and transport management.
3. Ultra-High Frequency (UHF) RFID Cards
Operating between 300 MHz and 3 GHz, UHF RFID cards offer affordability, making them ideal for asset tracking and inventory management.
4. Near Field Communication card NFC Card
An NFC card, short for Near Field Communication card, is a type of RFID card that allows devices like phones and smartwatches to exchange small bits of data with other devices and read NFC-equipped cards over relatively short distances.
The technology behind NFC is very similar to radio-frequency identification (RFID) commonly used in the security cards and keychain fobs that you likely already use to get into your office or gym. In fact, NFC is an evolution of RFID that offers more advanced features and better security.
NFC doesn’t require manual pairing or device discovery steps or passwords to deal with. All you need to do is place your smartphone within about four inches of another NFC device; it should immediately detect it and be ready to go.
If you’ve ever used Apple Pay, Google Pay, or Samsung Pay, then you’ve already taken advantage of the NFC feature on your phone. However, NFC can do a lot more than just handle mobile payments. For instance, it can be used for secure and contactless payment, ticketing, and data sharing applications.
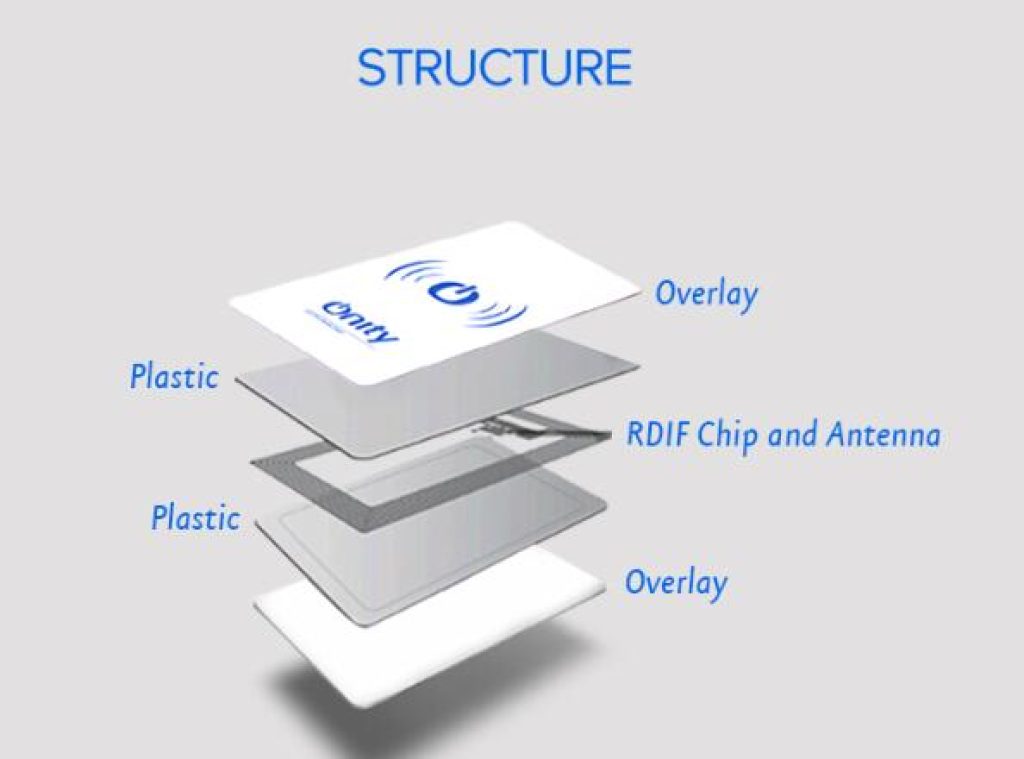
Components of RFID Cards
RFID Chip
The heart of an RFID card, a tiny chip holds identity and account details. Despite its small size, the chip can store vast amounts of data, requiring an external power source to operate.
| Chip | Memory | Protocol | Read/Write | ||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| TK4100 | 64bit | ISO7815 | Read-only | ||||||||||||||||
| EM4200 | 128bit | ISO7815 | Read-only | ||||||||||||||||
| EM4305 | 512bit | ISO11784/11785 | Read&Write | ||||||||||||||||
| EM4450 | 1kbit | ISO11784/11785 | Read&Write | ||||||||||||||||
| ATA5577 | 224bit | ISO11784/11785 | Read&Write | ||||||||||||||||
| Hitag 1 | 2048bit | ISO11784/11785 | Read&Write | ||||||||||||||||
| Hitag2 | 256bit | ISO11784/11785 | Read&Write | ||||||||||||||||
| MIFARE Classic 1k(S50) | 1K Bytes | ISO14443A | Read&Write | ||||||||||||||||
| MIFARE Classic 4k(S70) | 4K Bytes | ISO14443A | Read&Write | ||||||||||||||||
| MIFARE Ultralight EV 1 | 512bit | ISO14443A | Read&Write | ||||||||||||||||
| MIFARE Ultralight C | 192 Bytes | ISO14443A | Read&Write | ||||||||||||||||
| MIFARE Plus EV2(2K) | 2K Byte | ISO14443A | Read&Write | ||||||||||||||||
| MIFARE Plus EV2(4K) | 4K Bytes | ISO14443A | Read&Write | ||||||||||||||||
| MIFARE Plus SE(2K) | 2K Byte | ISO14443A | Read&Write | ||||||||||||||||
| MIFARE Plus SE(4K) | 4K Byte | ISO14443A | Read&Write | ||||||||||||||||
| MIFARE Plus X(2K) | 2K Byte | ISO14443A | Read&Write | ||||||||||||||||
| MIFARE Plus X(4K) | 4K Byte | ISO14443A | Read&Write | ||||||||||||||||
| MIFARE Desfire Light | 640 Bytes | ISO14443A | Read&Write | ||||||||||||||||
| MIFARE Desfire EV3(2K) | 2K Bytes | ISO14443A | Read&Write | ||||||||||||||||
| MIFARE Desfire EV3(4K) | 4K Bytes | ISO14443A | Read&Write | ||||||||||||||||
| MIFARE Desfire EV3(8K) | 8K Bytes | ISO14443A | Read&Write | ||||||||||||||||
| NTAG 213 | 144 Bytes | ISO14443A | Read&Write | ||||||||||||||||
| NTAG 215 | 504 Bytes | ISO14443A | Read&Write | ||||||||||||||||
| NTAG 216 | 888 Bytes | ISO14443A | Read&Write | ||||||||||||||||
| NTAG 213 Tag Temper | 144 Bytes | ISO14443A | Read&Write | ||||||||||||||||
| NTAG 424 DNA | 416 Bytes | ISO14443A | Read&Write | ||||||||||||||||
| NTAG 424 DNA Tag Tamper | 416 Bytes | ISO14443A | Read&Write | ||||||||||||||||
| ICODE SLIX | 896 bits | ISO15693/ISO 18000-3M1 | Read&Write | ||||||||||||||||
| ICODE SLIX 2 | 2528 bits | ISO15693/ISO 18000-3M1 | Read&Write | ||||||||||||||||
| ICODE SLIX-L | 256 bits | ISO15693/ISO 18000-3M1 | Read&Write | ||||||||||||||||
| ICODE SLIX-S | 1280 bits | ISO15693/ISO 18000-3M1 | Read&Write | ||||||||||||||||
| ICODE DNA | 2016 bits | ISO15693/ISO 18000-3M1 | Read&Write | ||||||||||||||||
| Tag-It™ HF-I Standard (TI 256) | 256 Byte | ISO15693 | Read&Write | ||||||||||||||||
| Tag-It™ HF-I Plus (TI 2048) | 2K Bytes | ISO15693 | Read&Write | ||||||||||||||||
| Higgs 3 | 96 bit epc,512 bit user | EPC Class1 Gen2/ISO 18000 6C | Read&Write | ||||||||||||||||
| Higgs 4 | 128 bit epc,512 bit user | EPC Class1 Gen2/ISO 18000 6C | Read&Write | ||||||||||||||||
| MONZA 4QT | 128 bit epc,512 bit user | EPC Class1 Gen2/ISO 18000 6C | Read&Write | ||||||||||||||||
| Monza 5 | 128 bit epc,32 bit user | EPC Class1 Gen2/ISO 18000 6C | Read&Write | ||||||||||||||||
| Monza R6 | 96bit epc | EPC Class1 Gen2/ISO 18000 6C | Read&Write | ||||||||||||||||
| Monza R6-P | 96bit epc,32 bit user | EPC Class1 Gen2/ISO 18000 6C | Read&Write | ||||||||||||||||
| UCODE 7 | 128 bit epc | EPC Class1 Gen2/ISO 18000 6C | Read&Write | ||||||||||||||||
| UCODE 7m | 128 bit epc | EPC Class1 Gen2/ISO 18000 6C | Read&Write | ||||||||||||||||
| Ucode 8 | 128 bit epc | EPC Class1 Gen2/ISO 18000 6C | Read&Write | ||||||||||||||||
| Ucode 8m | 96 bit epc,32 bit user | EPC Class1 Gen2/ISO 18000 6C | Read&Write | ||||||||||||||||
| UCODE DNA | 224bit epc,3072 bit user | EPC Class1 Gen2/ISO 18000 6C | Read&Write |
Antenna
A minute metal coil enables communication between the chip and RFID reader by receiving and transmitting radio waves.
Substrate
The visible part of the card, typically made of plastic, provides structural support, holding the chip and antenna together.
How does RFID card work?
RFID cards work by using radio frequency waves to transfer data and identify objects. Here’s a step-by-step explanation of how an RFID card works:
- Tagging: Items are tagged with RFID tags, which contain a tiny radio transponder, a radio receiver, and a transmitter.
- Interrogation: When triggered by an electromagnetic interrogation pulse from a nearby RFID reader device, the tag transmits digital data, usually an identifying inventory number, back to the reader.
- Energy Source: Passive RFID tags, like those commonly found in RFID cards, are powered by energy from the RFID reader’s interrogating radio waves¹. Active tags, on the other hand, are powered by a battery and thus can be read at a greater range from the RFID reader, up to hundreds of meters.
- Data Transmission: The RFID reader amplifies energy, modulates it with data, and sends the energy at a certain frequency out to an RFID antenna. The ability to identify each individual RFID tag being read is all thanks to a unique identifier (unique information) in the RFID tag’s memory.
- Reading: Unlike a barcode, the tag does not need to be within the line of sight of the reader, so it may be embedded in the tracked object. RFID takes auto-ID technology to the next level by allowing tags to be read without line of sight and up to 30+ meters away.
It’s important to note that RFID technology is widely used in many industries, including healthcare, retail, hospitality, and manufacturing. It’s also used for tracking inventory, supply chain management, and even for identifying animals¹. However, the possibility of reading personally-linked information without consent has raised serious privacy concerns.
Applications of RFID Cards
1. Contactless Payments
In eateries and shopping outlets, RFID cards facilitate swift and convenient payments. The tap-and-go method expedites transactions, offering flexibility with options like wristbands and smartphones.
2. Access Control
Organizations employ RFID access cards for secure entry to restricted areas. The encrypted data on these cards ensures security, with options ranging from simple prox cards to advanced smart cards.
RFID Cards in Access Control

Efficient and secure, RFID access cards offer:
- Automated Control
RFID cards are widely used in access control systems to authenticate and grant or restrict access to individuals. Here’s how they work:
- RFID Tag: An RFID tag is installed in a door key card or gate fob, which residents use to gain access to the building.
- RFID Reader: Readers are installed near the door to which they manage access. They contain antennas, which receive data transmitted by RFID tags.
- Control Panel: The control panel is a computer server that reads and interprets the data passed along by the RFID reader.
In the context of door access systems, an RFID card door lock typically consists of a stationary reader and a key card or fob used to store access credentials. RFID technology uses electromagnetic waves to capture and read transmitted data. The information of a cardholder, object, or reader is electronically stored in the RFID cards or tags, which can contain small pieces of information such as identification numbers, prices, or codes.
RFID access control systems are widely used in various industries and are known for their reliability and durability. In commercial access control systems, RFID-enabled tags are usually attached to employees’ ID cards, or they are given unique access cards for their office. This provides a simple way for any company to deploy an access control solution that allows for unique credentials.
It’s important to note that while RFID cards provide a convenient and efficient means of access control, they are not immune to potential security threats. Therefore, it’s crucial to implement appropriate security measures to protect against unauthorized access.
2. Data Gathering Capabilities
3. Remote Management
4. Affordability and Scalability
Other Applications of RFID Cards
Beyond payments and access control, RFID cards find use in:
- Library Systems
RFID (Radio Frequency Identification) technology is widely used in library systems for various purposes:
- Identification and Security: RFID tags are placed in books and other library materials to speed up materials handling functions such as check-in and check-out, and to provide security for the items.
- Inventory Management: RFID technology enables libraries to automate the inventory process, eliminating the need for manual scanning of barcodes or other traditional methods³. The RFID tags can be attached to books, DVDs, and other materials, allowing them to be easily tracked and located.
- Self-Service: RFID technology allows for a more streamlined circulation and checkout process. When a patron checks out a book, the RFID tag is scanned, and the information is recorded in the library’s system³. This process is faster and more accurate than traditional methods, allowing for a smoother and more efficient transaction.
- Shelf Management: RFID technology supports electronic inventorying and shelf searching, making it easier for library staff to manage and locate materials.
RFID systems in libraries are composed of tags, readers, and middleware software. The systems rely heavily on the integrated library system (ILS), and the middleware is designed to support communication between the reader and the ILS. The tags are placed inside library material, on media cases, or on multipart set bags. The readers are placed at staff workstations and self-check machines and built into security gates.

2.Events Management
RFID cards are frequently used for event management due to their efficiency and convenience. Here are some of their applications:
- Access Control: RFID cards can control access to certain areas of an event based on purchases. For instance, only a person with a delegate pass is allowed entry to important conferences. RFID can also log the presence and entries of cards in any area of the event, allowing better security and tracing.
- Ticketing: RFID cards can replace traditional paper tickets, reducing the time visitors spend scrambling to find paper barcodes or crumpled tickets¹. This reduces traffic backup in and out of secured areas and enhances the customer experience.
- Prevention of Counterfeit Tickets: Embedded RFID tags prevent counterfeit tickets and illegal entry. Because RFID tags are incredibly secure, event personnel and staff can be assured that only authentic ticket holders can gain access to the event or specific areas.
- Payment Systems: RFID allows attendees to pay for food, drinks, and merchandise with their wristbands instead of carrying cash or credit cards⁵. It’s streamlined and safe, and makes checkout faster. Research shows that people spend up to 20% more at events when using RFID instead of cash.
- Real-Time Tracking: RFID cards enable real-time tracking of attendee behavior. Every interaction, from entry and exit times to purchases and booth visits, can be recorded³. This provides organizers with invaluable data and insights to improve future events.
- Efficiency: Faster admissions, less waiting, eliminates fraudulent ticket admissions, less personnel hiring required, automated scanning available.
- Data Collection: More available data in real-time and post-event to management and staff.
These are just a few examples of how RFID cards can be used in event management. The specific applications can vary depending on the nature of the event and the needs of the organizers.
3.Healthcare Management
RFID cards are extensively used in healthcare management for a variety of purposes:
- Patient Tracking: RFID patient wristbands are used to track patients in hospitals, improving security, identifying and addressing gaps in internal processes, improving bed allocation, updating doctors’ schedules, and enhancing patient satisfaction². Patient records on wristbands are commonly maintained and verified using passive RFID systems.
- Equipment Tracking: RFID technology allows healthcare providers to track the real-time location of medical equipment, which can help improve patient care and reduce costs.
- Inventory Control: RFID technology enables automated inventory management, reducing the time and effort required to track medical supplies and equipment
- Access Control: RFID cards are used to control access to certain areas in a healthcare facility, enhancing security and ensuring that only authorized personnel can access sensitive areas.
- Data System: RFID cards power a connected data system, encouraging the use of electronic records available for every authorized user, wherever they may be³. Providers have 24/7 access to patient data from all sources, including primary care doctors, medical devices, and even pharmacies.
These are just a few examples of how RFID cards are used in healthcare management. The specific applications can vary depending on the needs of the healthcare facility.
4. Transport Management
RFID cards are extensively used in transport management for a variety of purposes:
- Ticketing: RFID ticket cards can replace traditional paper tickets, reducing the time visitors spend scrambling to find paper barcodes or crumpled tickets. This reduces traffic backup in and out of secured areas and enhances the customer experience.
- Access Control: RFID cards can control access to certain areas of a transport based on purchases. For instance, only a person with a delegate pass is allowed entry to important conferences⁴. RFID can also log the presence and entries of cards in any area of the event, allowing better security and tracing.
- Fleet Management: In real-time fleet management systems, the RFID system enables driver registration and identification⁴. On top of the device, it is required to install an accessory named reader, serving the purpose to read the card assigned to drivers registered in the platform.
- Inventory Control: RFID technology enables automated inventory management, reducing the time and effort required to track transport supplies and equipment.
- Data System: RFID cards power a connected data system, encouraging the use of electronic records available for every authorized user, wherever they may be³. Providers have 24/7 access to transport data from all sources, including primary care drivers, transport devices, and even pharmacies.
These are just a few examples of how RFID cards are used in transport management. The specific applications can vary depending on the needs of the transport facility.
How secure are RFID cards?
RFID cards are generally considered to be secure, but like any technology, they are not completely immune to potential security threats.
Security of RFID Cards:
- RFID credit cards are considered to be as safe as EMV chip cards¹.
- Data theft concerning RFID cards is uncommon.
- This is because of how these cards transmit information and what information is shared.
- Unlike traditional credit cards, RFID cards use one-time codes to complete each transaction.
Potential Threats:
- RFID can be susceptible to hackers because the interaction between the RFID chip and the reader can be done with no authentication.
- This leaves the system open to man-in-the-middle attacks and spoofing.
- More modern RFID cards are equipped with added security to prevent malicious attacks.
Protection Measures:
- Tech companies have built products to protect RFID cards like wallets and protective sleeves that prevent criminals from swiping your data.
- As a result, it’s important to be constantly aware of your surroundings when using RFID-enabled credit cards.
- Before using your card, look around you for any suspicious people or activities.
- Consider using an alternate payment method if you have any reason to doubt.
- RFID sleeves and shield wallets are another option for added security.
In conclusion, while RFID cards are generally secure, it’s always important to take precautions to protect your personal information.
Can RFID cards be cloned or hacked?
Yes, RFID cards can potentially be cloned or hacked, but the likelihood and ease of this happening depend on the type of RFID technology used and the security measures in place.
Cloning RFID Cards:
- If a transit company is issuing transponders with unique serial numbers and allowing people to ride its buses as long as the ID in a transponder appears valid, then a criminal could buy an RFID card on the Internet, write the ID of a legitimate card to the transponder with an RFID reader-writer and then use it like the original.
- This would not require a lot of technical skill.
- However, there are ways to prevent this kind of fraud.
Hacking RFID Cards:
- Hackers using RFID scanners can theoretically steal money via your phone’s tap-to-pay app.
- As some chips are rewritable, hackers can even delete or replace RFID information with their own data.
- It’s not too tricky for a hacker to build his or her own RFID scanner if they wanted to.
Protection Measures:
- Tech companies have built products to protect RFID cards like wallets and protective sleeves that prevent criminals from swiping your data².
- As a result, it’s important to be constantly aware of your surroundings when using RFID-enabled credit cards.
- Before using your card, look around you for any suspicious people or activities.
- Consider using an alternate payment method if you have any reason to doubt.
- RFID sleeves and shield wallets are another option for added security.
In conclusion, while RFID cards can potentially be cloned or hacked, there are measures that can be taken to protect against this. It’s always important to take precautions to protect your personal information.
What is the range of an RFID card?
The range of an RFID card can vary greatly depending on the type of card and the frequency it operates at:
- Low Frequency (LF) RFID Cards: These cards operate at 125 KHz and typically have a reading distance of 1-2 cm.
- High Frequency (HF) RFID Cards: These cards operate at 13.56 MHz and can have a reading distance of up to 10 cm.
- Ultra-High Frequency (UHF) RFID Cards: These cards operate at 860-960 MHz and can have a reading distance of 1-20 meters. However, with a passive RFID tag, UHF RFID cards can read at ranges as far as 12 meters, whereas active tags can achieve ranges of 100 meters or more.
It’s important to note that these ranges are approximate and can be influenced by factors such as the power of the RFID reader, interference from other devices, and the environment in which the card is being used.
What is the lifespan of an RFID card?
The lifespan of an RFID card can vary greatly depending on several factors, including the physical durability of the card, the environmental conditions in which it is used, and the frequency of use.
Under normal conditions, RFID-enabled cards can function for 20 years or more. If the antenna and chip are not exposed to high heat levels or harsh chemicals, the cards will be functional for a long time. However, active RFID tags, which carry their own power supply in the form of a battery, typically last between one and three years.
It’s important to note that RFID cards can stop working if the card is physically damaged, demagnetized, or exposed to electrostatic discharge (ESD). Therefore, it is recommended to use an RFID sleeve or wallet to prevent physical contact of the card with other credit cards.
















